As software projects grow more complex daily, the dependencies we need in the projects have also become numerous. Many projects depend on numerous external libraries and frameworks, which can make it difficult for us to keep track of potential vulnerabilities. To mitigate those risks, the OWASP Dependency Check tool can be used to scan your project and identify any known vulnerabilities in its dependencies. So, In this post, we will see how to use OWASP Dependency Check to detect vulnerabilities in a Maven project.
What is OWASP Dependency Check?
OWASP Dependency Check is a tool that identifies known vulnerabilities in a project’s dependencies. It can be used with many different programming languages and build tools, such as Gradle/Maven. The tool uses a database of known vulnerabilities to compare against the dependencies in your project and generates a report of any potential risks.
Setting up OWASP Dependency Check with Maven:
To use OWASP Dependency Check with Maven, you’ll need to add it as a plugin to your pom.xml file. Here’s an example of what that might look like:
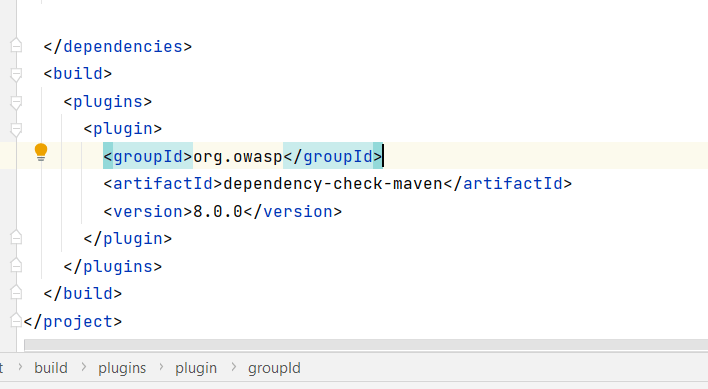
<build>
<plugins>
<plugin>
<groupId>org.owasp</groupId>
<artifactId>dependency-check-maven</artifactId>
<version>8.0.0</version>
</plugin>
</plugins>
</build>
Once you’ve added the plugin to your pom.xml, you can run the scan by executing the following command in your terminal:
mvn dependency-check:check
This will generate a report in HTML format that can be viewed in your web browser.
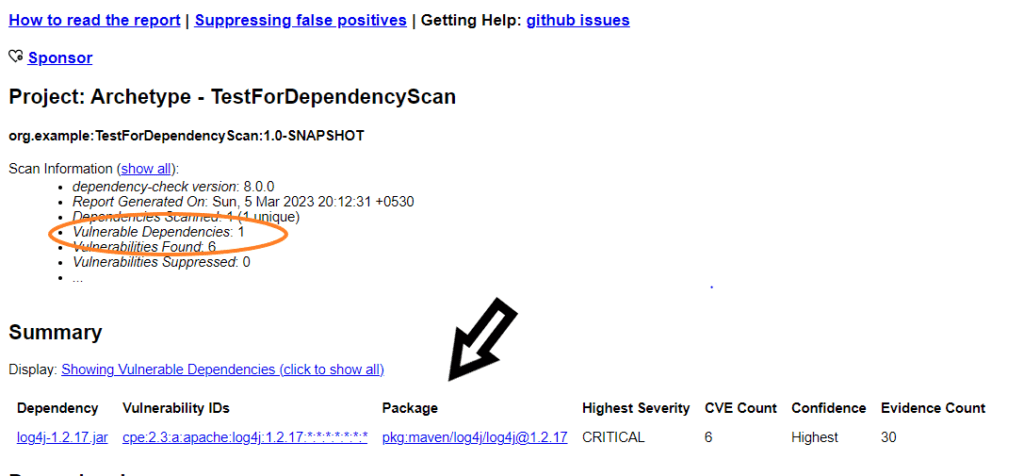
Interpreting the OWASP Dependency Check Report:
The OWASP Dependency Check report provides a list of all dependencies in your project and their associated vulnerabilities. Each vulnerability is given a severity rating, which can help you prioritize which issues to address first. The report also provides links to additional information about each vulnerability, including its CVE (Common Vulnerabilities and Exposures) ID and a description of the risk.
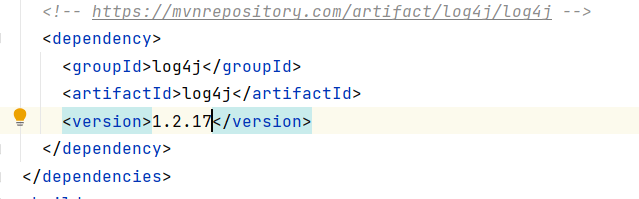
Mitigating Vulnerabilities:
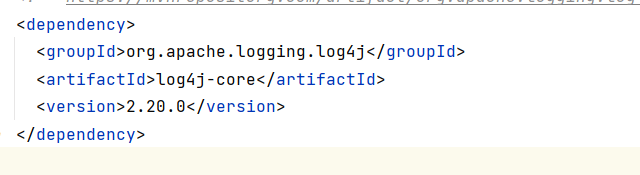
Once you’ve identified vulnerabilities in your project, it’s important to take steps to mitigate them. Depending on the severity of the issue, you may need to update the dependency to a newer version that has been patched. In some cases, you may need to remove the dependency altogether and find an alternative library that doesn’t have the same vulnerability. It’s important to weigh the risk and potential impact of each vulnerability and make a plan to address them accordingly.

Conclusion:
Using OWASP Dependency Check to detect vulnerabilities in your Maven project can help you upfront identify and mitigate any potential security risks in your projects. By regularly running scans and addressing any vulnerabilities that are identified, you can ensure that your project remains secure and protected from external threats.
